J1 (cipher): Difference between revisions
No edit summary |
m (43 revisions imported) |
||
| (35 intermediate revisions by one other user not shown) | |||
| Line 2: | Line 2: | ||
| name = J1 (Nisan) | | name = J1 (Nisan) | ||
| image = File:6-Figure3.2-1.png | | image = File:6-Figure3.2-1.png | ||
| caption = A contracting unbalanced Feistel network | | caption = A generic contracting unbalanced Feistel network, similar to J1. | ||
| designers = [[Air Force Intelligence Directorate | | designers = Unit 28, <br>[[Air Force Intelligence Directorate]] | ||
| publish date = 1974 ( | | publish date = 1974 (issued)<br> 1998 (declassified) | ||
| derived from = | | derived from = | ||
| derived to = | | derived to = | ||
| Line 12: | Line 12: | ||
| structure = {{wpl|Unbalanced Feistel network}} | | structure = {{wpl|Unbalanced Feistel network}} | ||
| rounds = 127 | | rounds = 127 | ||
| cryptanalysis = | | cryptanalysis = Correlation attack using 2<sup>45</sup> ciphertext characters against several weak long-term keys. As of 2018, no feasible attack has been found against long-term keys used operationally. | ||
}} | }} | ||
The '''J1''' cipher, also known by its code name of '''''Nisan''''' (Arabic: نيسان, English: {{wpl|April}}), is a {{wpl|symmetric key}} {{wpl|block cipher}} with a key length of 242 bits and a block size of 36 bits. It was developed by Unit 28 (Cryptography) of the Riysian Air Force Intelligence Directorate (Mukhabarat) as a cipher for the encryption of military, government, and diplomatic teletype and later data networks. The algorithm was issued in 1974, but due to its sensitive nature, it was only declassified in 1998, after it had been | The '''J1''' cipher, also known by its code name of '''''Nisan''''' (Arabic: نيسان, English: {{wpl|April}}), is a {{wpl|symmetric key}} {{wpl|block cipher}} with a key length of 242 bits and a block size of 36 bits. It was developed by Unit 28 (Cryptography) of the Riysian Air Force Intelligence Directorate (Mukhabarat) as a cipher for the encryption of military, government, and diplomatic teletype and later data networks. The algorithm was issued in 1974, but due to its sensitive nature, it was only declassified in 1998, after the hardware using it had largely been retired. It is notable for being the first Riysian block cipher, the first Riysian cipher designed for digital/electronic encryption, and for using a structure similar to an unbalanced Feistel network, which was considered highly complex in its time. | ||
Though it has been superseded by more modern algorithms, the J1 continues to make a substantial impact on Riysian cryptography. Lessons learned from its development and cryptanalysis continue to be utilized in the development of cipher algorithms, as well as some of its underlying concepts. In particular, the concept of the unbalanced Feistel cipher remains very popular, with even the recent [[J3 (cipher)|J3]] algorithm using a modified Feistel network. | |||
==History== | ==History== | ||
Mixers, also known as one-time tape machines, provide encrypted point-to-point communications through the use of a {{wp|one-time tape}}. Such systems had been first deployed back in World War 2, and their development and usage only continued to grow in the decades following the war. In theory, such a system is cryptographically unbreakable, making it a very useful and successful system for secure communications. However, the same principles that made it secure also made key management very difficult, and only really suited for high-level communications. | |||
In contrast, at the operational-tactical level the electromechanical cipher machine - such as the {{wp|Enigma machine}} of World War 2 - was still king. These machines had the information speed and flexibility for encrypted point-to-point communications at lower levels. However, their design and key management was inherently much less secure than a one-time tape, and the rapid advancement of computer technology during the early Cold War era threatened to make them even more vulnerable to cracking than they already were. | |||
By the late 1960s, the Riysian ''[[Hay'at al-Arkan]]'' had become concerned about the resilience and security of its communications during a major conflict. The next war was predicted to be fast, mobile, and fluid, for which they needed encryption that would be easy to manage. At the same time, the Hay'at al-Arkan required a high level of security, as the current system of electromechanical cipher machines was liable to being "broken" or captured by an enemy - a fear that was partially proven correct during the [[Riysian Unification War]] in 1973. | |||
With the help of the Riysian Deuxième Bureau and the [[Air Force Intelligence Directorate]], the latter having had the most experience in cryptography, the Hay'at al-Arkan issued a requirement for its new cipher in 1970. The requirements included "near-perfect" security, being usable for point-to-point and general communications, and the ability to cipher both online and offline plain text. Work on the cipher started in 1971 with a small team of cryptographers from the Air Force Intelligence Directorate's Unit 28, and the accompanying cipher machine in 1972. The new cipher, termed "J1", would be a revolution in Riysian cryptography, with the team using the latest in cryptography and computer science to create a whole new class of cipher system. Originally planned for initial release in 1973, the Unification War and the subsequent reorganization of the Riysian intelligence services into the Directorate caused it to be delayed until 1974, when it was introduced with the accompanying AT-262 cipher machine. | |||
==Description== | ==Description== | ||
[[File:J1ltk.jpg|250px|thumb| | [[File:J1ltk.jpg|250px|thumb|A J1 long-term key.]] | ||
J1 uses a block size of 36 bits, with a key size of 242 bits and an {{wpl|initialization vector}} (IV) of 61 bits randomly generated from an {{wpl|LSFR}}. The internal structure is similar to an unbalanced Feistel network, with four branches and 127 rounds. Its key schedule is very simple, forming two subkeys each 121 bits in length by splitting the main key in half, with a periodic repetition every 121 rounds. Like most ciphers of its age, it | J1 uses a block size of 36 bits, with a key size of 242 bits and an {{wpl|initialization vector}} (IV) of 61 bits randomly generated from an {{wpl|LSFR}}. The internal structure is similar to an unbalanced Feistel network, with four branches and 127 rounds. Its key schedule is very simple, forming two subkeys each 121 bits in length by splitting the main key in half, with a periodic repetition every 121 rounds. Like most ciphers of its age, it was implemented in specific hardware; however, by being an electronic cipher, it is possible to recreate it through software only. | ||
An unusual feature of the J1 cipher is that it accepts two keys, a short-term key and a plug-in long-term key. The short-term key is the nominal secret key for encryption, while the long-term key is a printed circuit board with unique wiring per series. This long-term key performs a function similar to both the {{wpl|S-box}}es and {{wpl|Permutation box|P-box}} of modern block ciphers, accepting 9 individual inputs - each similar to an S-box - of 4 bits each, and then performing a permutation as in a P-box. The | An unusual feature of the J1 cipher is that it accepts two keys, a short-term key and a plug-in long-term key. The short-term key is the nominal secret key for encryption, while the long-term key is a printed circuit board with unique wiring per series. This long-term key performs a function similar to both the {{wpl|S-box}}es and {{wpl|Permutation box|P-box}} of modern block ciphers, accepting 9 individual inputs - each similar to an S-box - of 4 bits each, and then performing a permutation as in a P-box. One of the key halves would be used in the S-box-like function, while the other half and the IV would be used in the P-box-like function. The implementation of the long-term key is similar to the concept of a {{wpl|Tweakable block cipher|tweak}}. The long term key has an effective size of anywhere from 83 to 94 bits, depending on the key's wiring. | ||
Though designed as a block cipher, J1 was almost always used in a stream cipher mode. When used as a stream cipher, the block cipher is run through its full 127 cycles, with a function on the long-term key circuit board extracting a single bit. To encrypt a single 5-bit {{wpl|Baudot code#ITA2|Baudot character}}, 13 bits are required, for a total of 1,651 cycles; 3 bits of these 13 are randomly chosen to be dropped, with the remaining 10 bits used to doubly-encrypt the character in a 5+5 scheme. As the IV is needed in the decryption process, the 61-bit IV would be transmitted in the clear as part of a 125-bit/25-character "synchronization sequence". | Though designed as a block cipher, J1 was almost always used in a stream cipher mode. When used as a stream cipher, the block cipher is run through its full 127 cycles, with a function on the long-term key circuit board extracting a single bit. To encrypt a single 5-bit {{wpl|Baudot code#ITA2|Baudot character}}, 13 bits are required, for a total of 1,651 cycles; 3 bits of these 13 are randomly chosen to be dropped, with the remaining 10 bits used to doubly-encrypt the character in a 5+5 scheme. As the IV is needed in the decryption process, the 61-bit IV would be transmitted in the clear as part of a 125-bit/25-character "synchronization sequence". | ||
| Line 29: | Line 39: | ||
==Cryptanalysis== | ==Cryptanalysis== | ||
Despite its age, | Despite its age, J1 remains a substantially strong algorithm, especially when compared to some of its contemporaries such as {{wpl|DES}}. This is largely thanks both to the large number of rounds used and the extremely low number of bits generated during encryption, as well as the use of a long-term key. The long key length of 242 bits also helps to increases security. Analysis of some of the publicly available long-term keys indicate that the bits were specifically chosen with the goal of defending against basic {{wpl|differential cryptanalysis|differential}} and {{wpl|linear cryptanalysis}}, nearly 20 years before the techniques were publicly discovered, but around the same time that major intelligence agencies around the world became aware of it. | ||
However, the security of the J1 cipher is heavily dependent on the long-term key; overall weak long-term keys can open up the cipher to a variety of attacks. Furthermore, the simple, periodic key schedule allows for some strong correlation attacks against the cipher despite the presence of a randomly generated IV. To protect against these potential weaknesses, a J1 long-term key must historically meet 40 different design requirements. Most - but not all - keys delivered to military and diplomatic systems met these requirements, but the stringent requirements significantly increased the difficulty and cost of manufacturing them. | |||
Currently, the best attack against J1 is a {{wpl|correlation attack}} published in January 2018, which uses 2<sup>45</sup> ciphertext characters to break a number of weak long-term keys. Long-term keys that were known to have been used operationally were found to be strongly resistant to this attack. Due to this difference, J1 is not yet considered broken. | |||
==Technology/Hardware== | ==Technology/Hardware== | ||
[[File:At262.jpg|250px|thumb|An AT-262A with an AK-120 teletype/printer.]] | |||
The J1 was created specifically for the AT-262 family of encryption machines, the first Riysian digital electronic - as opposed to analog or electromechanical - cipher machines. These were highly successful, being used throughout the Armed Forces and government ministries, as well as for diplomatic communication with embassies. | |||
===AT-262A=== | |||
The AT-262A is the first and main member of the AT-262 family. It is an cipher machine used for both online and offline point-to-point communications by means of teletype, designed to replace old electromechanical cipher machines in that role. Combined with its control panel it weighs 45 kilograms, is capable of both asynchronous and synchronous transmission, with transmission speeds of either 50 or 100 baud (up to 200 baud) respectively, and can operate in duplex or half-duplex mode. The short-term key takes the form of a punched card, which is inserted into a card reader in the machine and is changed regularly, while the long-term key is inserted into the machine as a plug-in board and is only changed when necessary. It was capable of operating in an "quiet" mode, where it would automatically go online upon receipt of an encrypted telex, and decipher and print it out. | |||
It was generally used with the '''AK-120''' semi-electronic teletype/teleprinter machine, which featured an electronic keyboard and encoding, but an electromechanical matrix-type printer and opto-electronic tape reader. It could be operated with all components - keyboard, tape reader, and printer - together, as a standalone printer, or with only the keyboard or tape reader. Weight with all components together is 40 kilograms, and speed rate is adjustable to 50, 75, or 100 baud. Both the AK-120 and AT-262A were "caged" by metal casings in the field, and rated as not having enough EM emissions to warrant operating restrictions. The AT-262A was designed to be "future-proof", so other, later teletype machines could be used, though speed would always be limited to 200 baud. | |||
This was by far the most popular model, with just under 4,000 being produced in total from 1974 to 1982 at a peak rate of 50 machines a month. AT-262As were used for internal government communication, for communication with foreign embassies and consulates, Ministry of Interior communications, and on the operational level upwards in the Armed Forces. These machines remained in service until the early 1990s, being replaced by modern systems capable of handling higher data rates, but some remained in diplomatic and administrative service until the mid 2000s. | |||
===AT-262B=== | |||
The AT-262B was the first attempt to improve on the AT-262 design, and is the second member of the AT-262 family. Faced with ever increasing data usage, this version was designed to be able to encode/decode point-to-point data signals in ITA5/ASCII 8-bit code, in addition to the 5-bit Baudot code teleprinter messages from the original AT-262A. In order to keep costs down, it was designed to have minimal changes compared to the AT-262A, which would also allow for the older model to be upgraded rather than merely replaced. As the AT-262 could only recognize 5-bit code, ITA5 signals had to be converted to ITA2 Baudot before coding, encrypted as 5-bit Baudot, and then re-converted back to 8-bit code, which constrained the maximum data rate of the AT-262B to 100 baud as with teletype signals. | |||
Only 70 machines were built in 1983, and a further 80 were upgraded from 1983-1984. This model didn't achieve the popularity as its predecessor, as dedicated data encryption units with better performance than the AT-262B were already entering widespread military use by 1984. Most machines went to the Navy and Air Force, with all being used in the military. | |||
===AT-262T=== | |||
The third and final variant of the AT-262 family is the AT-262T. Much like the AT-262B, the AT-262T was designed to provide data encryption on top of teletype encryption, extending its useful lifespan. In addition, its internal speed was planned to be increased to 2.4 kbps using 8-bit ASCII code, with 5-bit Baudot being depreciated. It was to be used in conjunction with the in-development AK-144 modem, which provides teletype-like text and data, encoded in 8-bit ASCII. Though the AK-144 was released in 1992, there was no real interest or demand for an upgraded AT-262, especially as many had already been replaced by all-digital devices, so the AT-262T was never fielded. | |||
[[Category:Air Force Intelligence Directorate cryptography]] | [[Category:Air Force Intelligence Directorate cryptography]] | ||
Latest revision as of 23:27, 25 February 2019
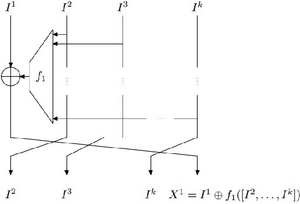 A generic contracting unbalanced Feistel network, similar to J1. | |
| General | |
|---|---|
| Designers | Unit 28, Air Force Intelligence Directorate |
| First published | 1974 (issued) 1998 (declassified) |
| Cipher detail | |
| Key sizes | 242 bits |
| Block sizes | 36 bits |
| Structure | Unbalanced Feistel network |
| Rounds | 127 |
| Best public cryptanalysis | |
| Correlation attack using 245 ciphertext characters against several weak long-term keys. As of 2018, no feasible attack has been found against long-term keys used operationally. | |
The J1 cipher, also known by its code name of Nisan (Arabic: نيسان, English: April), is a symmetric key block cipher with a key length of 242 bits and a block size of 36 bits. It was developed by Unit 28 (Cryptography) of the Riysian Air Force Intelligence Directorate (Mukhabarat) as a cipher for the encryption of military, government, and diplomatic teletype and later data networks. The algorithm was issued in 1974, but due to its sensitive nature, it was only declassified in 1998, after the hardware using it had largely been retired. It is notable for being the first Riysian block cipher, the first Riysian cipher designed for digital/electronic encryption, and for using a structure similar to an unbalanced Feistel network, which was considered highly complex in its time.
Though it has been superseded by more modern algorithms, the J1 continues to make a substantial impact on Riysian cryptography. Lessons learned from its development and cryptanalysis continue to be utilized in the development of cipher algorithms, as well as some of its underlying concepts. In particular, the concept of the unbalanced Feistel cipher remains very popular, with even the recent J3 algorithm using a modified Feistel network.
History
Mixers, also known as one-time tape machines, provide encrypted point-to-point communications through the use of a one-time tape. Such systems had been first deployed back in World War 2, and their development and usage only continued to grow in the decades following the war. In theory, such a system is cryptographically unbreakable, making it a very useful and successful system for secure communications. However, the same principles that made it secure also made key management very difficult, and only really suited for high-level communications.
In contrast, at the operational-tactical level the electromechanical cipher machine - such as the Enigma machine of World War 2 - was still king. These machines had the information speed and flexibility for encrypted point-to-point communications at lower levels. However, their design and key management was inherently much less secure than a one-time tape, and the rapid advancement of computer technology during the early Cold War era threatened to make them even more vulnerable to cracking than they already were.
By the late 1960s, the Riysian Hay'at al-Arkan had become concerned about the resilience and security of its communications during a major conflict. The next war was predicted to be fast, mobile, and fluid, for which they needed encryption that would be easy to manage. At the same time, the Hay'at al-Arkan required a high level of security, as the current system of electromechanical cipher machines was liable to being "broken" or captured by an enemy - a fear that was partially proven correct during the Riysian Unification War in 1973.
With the help of the Riysian Deuxième Bureau and the Air Force Intelligence Directorate, the latter having had the most experience in cryptography, the Hay'at al-Arkan issued a requirement for its new cipher in 1970. The requirements included "near-perfect" security, being usable for point-to-point and general communications, and the ability to cipher both online and offline plain text. Work on the cipher started in 1971 with a small team of cryptographers from the Air Force Intelligence Directorate's Unit 28, and the accompanying cipher machine in 1972. The new cipher, termed "J1", would be a revolution in Riysian cryptography, with the team using the latest in cryptography and computer science to create a whole new class of cipher system. Originally planned for initial release in 1973, the Unification War and the subsequent reorganization of the Riysian intelligence services into the Directorate caused it to be delayed until 1974, when it was introduced with the accompanying AT-262 cipher machine.
Description
J1 uses a block size of 36 bits, with a key size of 242 bits and an initialization vector (IV) of 61 bits randomly generated from an LSFR. The internal structure is similar to an unbalanced Feistel network, with four branches and 127 rounds. Its key schedule is very simple, forming two subkeys each 121 bits in length by splitting the main key in half, with a periodic repetition every 121 rounds. Like most ciphers of its age, it was implemented in specific hardware; however, by being an electronic cipher, it is possible to recreate it through software only.
An unusual feature of the J1 cipher is that it accepts two keys, a short-term key and a plug-in long-term key. The short-term key is the nominal secret key for encryption, while the long-term key is a printed circuit board with unique wiring per series. This long-term key performs a function similar to both the S-boxes and P-box of modern block ciphers, accepting 9 individual inputs - each similar to an S-box - of 4 bits each, and then performing a permutation as in a P-box. One of the key halves would be used in the S-box-like function, while the other half and the IV would be used in the P-box-like function. The implementation of the long-term key is similar to the concept of a tweak. The long term key has an effective size of anywhere from 83 to 94 bits, depending on the key's wiring.
Though designed as a block cipher, J1 was almost always used in a stream cipher mode. When used as a stream cipher, the block cipher is run through its full 127 cycles, with a function on the long-term key circuit board extracting a single bit. To encrypt a single 5-bit Baudot character, 13 bits are required, for a total of 1,651 cycles; 3 bits of these 13 are randomly chosen to be dropped, with the remaining 10 bits used to doubly-encrypt the character in a 5+5 scheme. As the IV is needed in the decryption process, the 61-bit IV would be transmitted in the clear as part of a 125-bit/25-character "synchronization sequence".
Cryptanalysis
Despite its age, J1 remains a substantially strong algorithm, especially when compared to some of its contemporaries such as DES. This is largely thanks both to the large number of rounds used and the extremely low number of bits generated during encryption, as well as the use of a long-term key. The long key length of 242 bits also helps to increases security. Analysis of some of the publicly available long-term keys indicate that the bits were specifically chosen with the goal of defending against basic differential and linear cryptanalysis, nearly 20 years before the techniques were publicly discovered, but around the same time that major intelligence agencies around the world became aware of it.
However, the security of the J1 cipher is heavily dependent on the long-term key; overall weak long-term keys can open up the cipher to a variety of attacks. Furthermore, the simple, periodic key schedule allows for some strong correlation attacks against the cipher despite the presence of a randomly generated IV. To protect against these potential weaknesses, a J1 long-term key must historically meet 40 different design requirements. Most - but not all - keys delivered to military and diplomatic systems met these requirements, but the stringent requirements significantly increased the difficulty and cost of manufacturing them.
Currently, the best attack against J1 is a correlation attack published in January 2018, which uses 245 ciphertext characters to break a number of weak long-term keys. Long-term keys that were known to have been used operationally were found to be strongly resistant to this attack. Due to this difference, J1 is not yet considered broken.
Technology/Hardware
The J1 was created specifically for the AT-262 family of encryption machines, the first Riysian digital electronic - as opposed to analog or electromechanical - cipher machines. These were highly successful, being used throughout the Armed Forces and government ministries, as well as for diplomatic communication with embassies.
AT-262A
The AT-262A is the first and main member of the AT-262 family. It is an cipher machine used for both online and offline point-to-point communications by means of teletype, designed to replace old electromechanical cipher machines in that role. Combined with its control panel it weighs 45 kilograms, is capable of both asynchronous and synchronous transmission, with transmission speeds of either 50 or 100 baud (up to 200 baud) respectively, and can operate in duplex or half-duplex mode. The short-term key takes the form of a punched card, which is inserted into a card reader in the machine and is changed regularly, while the long-term key is inserted into the machine as a plug-in board and is only changed when necessary. It was capable of operating in an "quiet" mode, where it would automatically go online upon receipt of an encrypted telex, and decipher and print it out.
It was generally used with the AK-120 semi-electronic teletype/teleprinter machine, which featured an electronic keyboard and encoding, but an electromechanical matrix-type printer and opto-electronic tape reader. It could be operated with all components - keyboard, tape reader, and printer - together, as a standalone printer, or with only the keyboard or tape reader. Weight with all components together is 40 kilograms, and speed rate is adjustable to 50, 75, or 100 baud. Both the AK-120 and AT-262A were "caged" by metal casings in the field, and rated as not having enough EM emissions to warrant operating restrictions. The AT-262A was designed to be "future-proof", so other, later teletype machines could be used, though speed would always be limited to 200 baud.
This was by far the most popular model, with just under 4,000 being produced in total from 1974 to 1982 at a peak rate of 50 machines a month. AT-262As were used for internal government communication, for communication with foreign embassies and consulates, Ministry of Interior communications, and on the operational level upwards in the Armed Forces. These machines remained in service until the early 1990s, being replaced by modern systems capable of handling higher data rates, but some remained in diplomatic and administrative service until the mid 2000s.
AT-262B
The AT-262B was the first attempt to improve on the AT-262 design, and is the second member of the AT-262 family. Faced with ever increasing data usage, this version was designed to be able to encode/decode point-to-point data signals in ITA5/ASCII 8-bit code, in addition to the 5-bit Baudot code teleprinter messages from the original AT-262A. In order to keep costs down, it was designed to have minimal changes compared to the AT-262A, which would also allow for the older model to be upgraded rather than merely replaced. As the AT-262 could only recognize 5-bit code, ITA5 signals had to be converted to ITA2 Baudot before coding, encrypted as 5-bit Baudot, and then re-converted back to 8-bit code, which constrained the maximum data rate of the AT-262B to 100 baud as with teletype signals.
Only 70 machines were built in 1983, and a further 80 were upgraded from 1983-1984. This model didn't achieve the popularity as its predecessor, as dedicated data encryption units with better performance than the AT-262B were already entering widespread military use by 1984. Most machines went to the Navy and Air Force, with all being used in the military.
AT-262T
The third and final variant of the AT-262 family is the AT-262T. Much like the AT-262B, the AT-262T was designed to provide data encryption on top of teletype encryption, extending its useful lifespan. In addition, its internal speed was planned to be increased to 2.4 kbps using 8-bit ASCII code, with 5-bit Baudot being depreciated. It was to be used in conjunction with the in-development AK-144 modem, which provides teletype-like text and data, encoded in 8-bit ASCII. Though the AK-144 was released in 1992, there was no real interest or demand for an upgraded AT-262, especially as many had already been replaced by all-digital devices, so the AT-262T was never fielded.

