J1 (cipher): Difference between revisions
No edit summary |
No edit summary |
||
| Line 15: | Line 15: | ||
}} | }} | ||
The '''J1''' cipher, also known by its code name of '''''Nisan''''' (Arabic: نيسان, English: {{wpl|April}}), is a {{wpl|symmetric key}} {{wpl|block cipher}} with a key length of 242 bits and a block size of 36 bits. It was developed by Unit 28 (Cryptography) of the Riysian Air Force Intelligence Directorate (Mukhabarat) as a cipher for the encryption of military, government, and diplomatic teletype and later data networks. The algorithm was issued in 1974, but due to its sensitive nature, it was only declassified in 1998, after it had been | The '''J1''' cipher, also known by its code name of '''''Nisan''''' (Arabic: نيسان, English: {{wpl|April}}), is a {{wpl|symmetric key}} {{wpl|block cipher}} with a key length of 242 bits and a block size of 36 bits. It was developed by Unit 28 (Cryptography) of the Riysian Air Force Intelligence Directorate (Mukhabarat) as a cipher for the encryption of military, government, and diplomatic teletype and later data networks. The algorithm was issued in 1974, but due to its sensitive nature, it was only declassified in 1998, after the hardware using it had largely been retired. It is notable for being the first fully electronic Riysian cipher, and for using a structure similar to an unbalanced Feistel network, which was considered highly complex in its time. | ||
Though it has been superseded by more modern algorithms such as the [[J2 (cipher)|J2]], the J1 . | |||
==History== | ==History== | ||
Revision as of 23:14, 22 May 2018
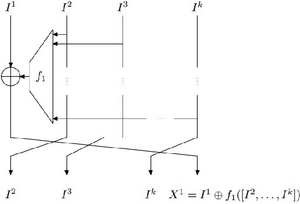 A contracting unbalanced Feistel network with 4 branches, like J1. | |
| General | |
|---|---|
| Designers | Unit 28, Air Force Intelligence Directorate |
| First published | 1974 (standardized) 1998 (declassified) |
| Cipher detail | |
| Key sizes | 242 bits |
| Block sizes | 36 bits |
| Structure | Unbalanced Feistel network |
| Rounds | 127 |
The J1 cipher, also known by its code name of Nisan (Arabic: نيسان, English: April), is a symmetric key block cipher with a key length of 242 bits and a block size of 36 bits. It was developed by Unit 28 (Cryptography) of the Riysian Air Force Intelligence Directorate (Mukhabarat) as a cipher for the encryption of military, government, and diplomatic teletype and later data networks. The algorithm was issued in 1974, but due to its sensitive nature, it was only declassified in 1998, after the hardware using it had largely been retired. It is notable for being the first fully electronic Riysian cipher, and for using a structure similar to an unbalanced Feistel network, which was considered highly complex in its time.
Though it has been superseded by more modern algorithms such as the J2, the J1 .
History
Description
J1 uses a block size of 36 bits, with a key size of 242 bits and an initialization vector (IV) of 61 bits randomly generated from an LSFR. The internal structure is similar to an unbalanced Feistel network, with four branches and 127 rounds. Its key schedule is very simple, forming two subkeys each 121 bits in length by splitting the main key in half, with a periodic repetition every 121 rounds. Like most ciphers of its age, it is implemented in specific hardware.
An unusual feature of the J1 cipher is that it accepts two keys, a short-term key and a plug-in long-term key. The short-term key is the nominal secret key for encryption, while the long-term key is a printed circuit board with unique wiring per series. This long-term key performs a function similar to both the S-boxes and P-box of modern block ciphers, accepting 9 individual inputs - each similar to an S-box - of 4 bits each, and then performing a permutation as in a P-box. The function of the long-term key is similar to the concept of a tweak.
Though designed as a block cipher, J1 was almost always used in a stream cipher mode. When used as a stream cipher, the block cipher is run through its full 127 cycles, with a function on the long-term key circuit board extracting a single bit. To encrypt a single 5-bit Baudot character, 13 bits are required, for a total of 1,651 cycles; 3 bits of these 13 are randomly chosen to be dropped, with the remaining 10 bits used to doubly-encrypt the character in a 5+5 scheme. As the IV is needed in the decryption process, the 61-bit IV would be transmitted in the clear as part of a 125-bit/25-character "synchronization sequence".
Cryptanalysis
Despite its age,
